Leak Details
Provides severity levels and risk scores for leaked information, visualizing response trends and damage fluctuations.
Risk levels are scored to easily set priorities, and monthly/yearly leak trend analysis allows objective verification of security investment effectiveness.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

Key Features
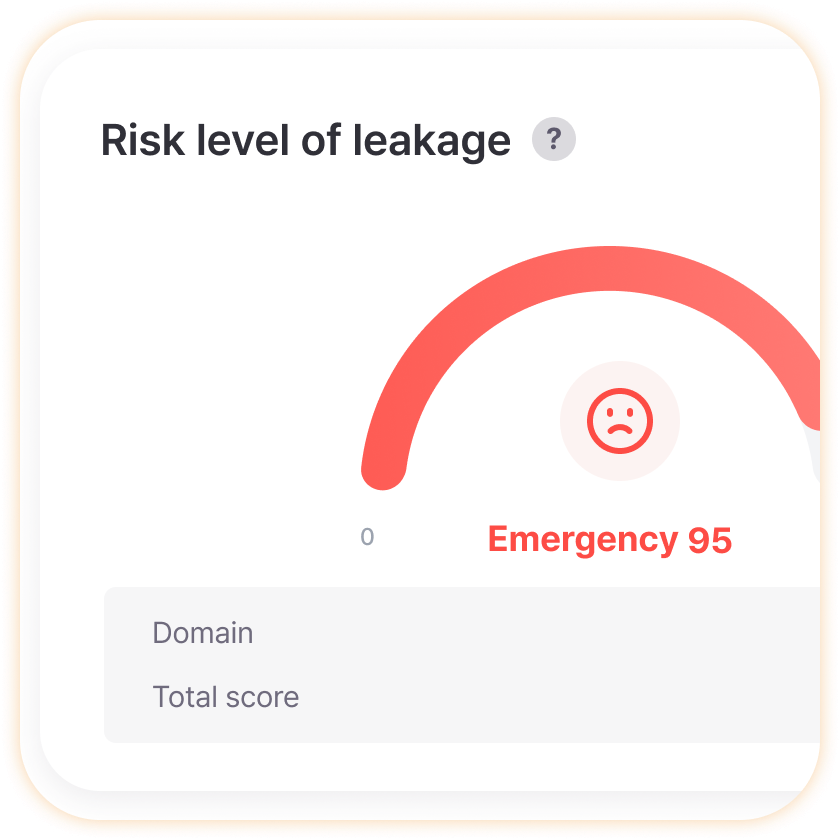
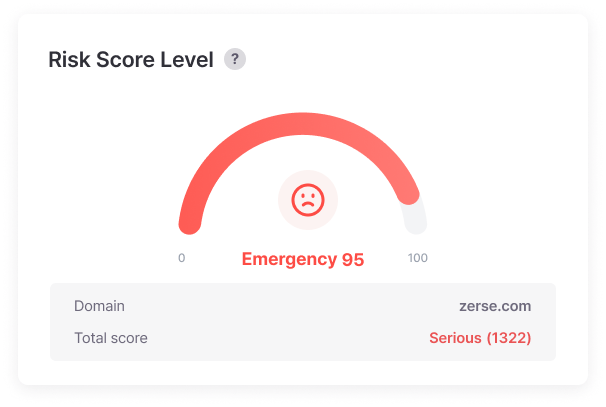
Leak Risk Level
Intuitively verify our company’s current risk level like a car speedometer, making it easy for even non-experts to understand the severity of situations. Anyone can understand that higher numbers mean more danger, and when reporting to management, you can clearly communicate current situations and investment needs with just one graph without complex explanations.
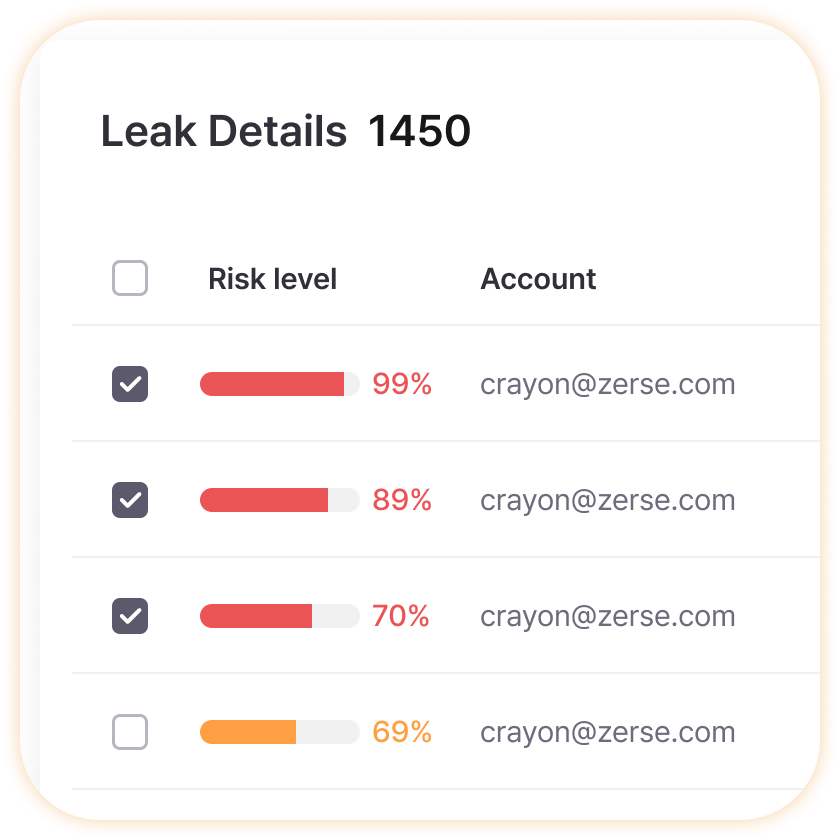
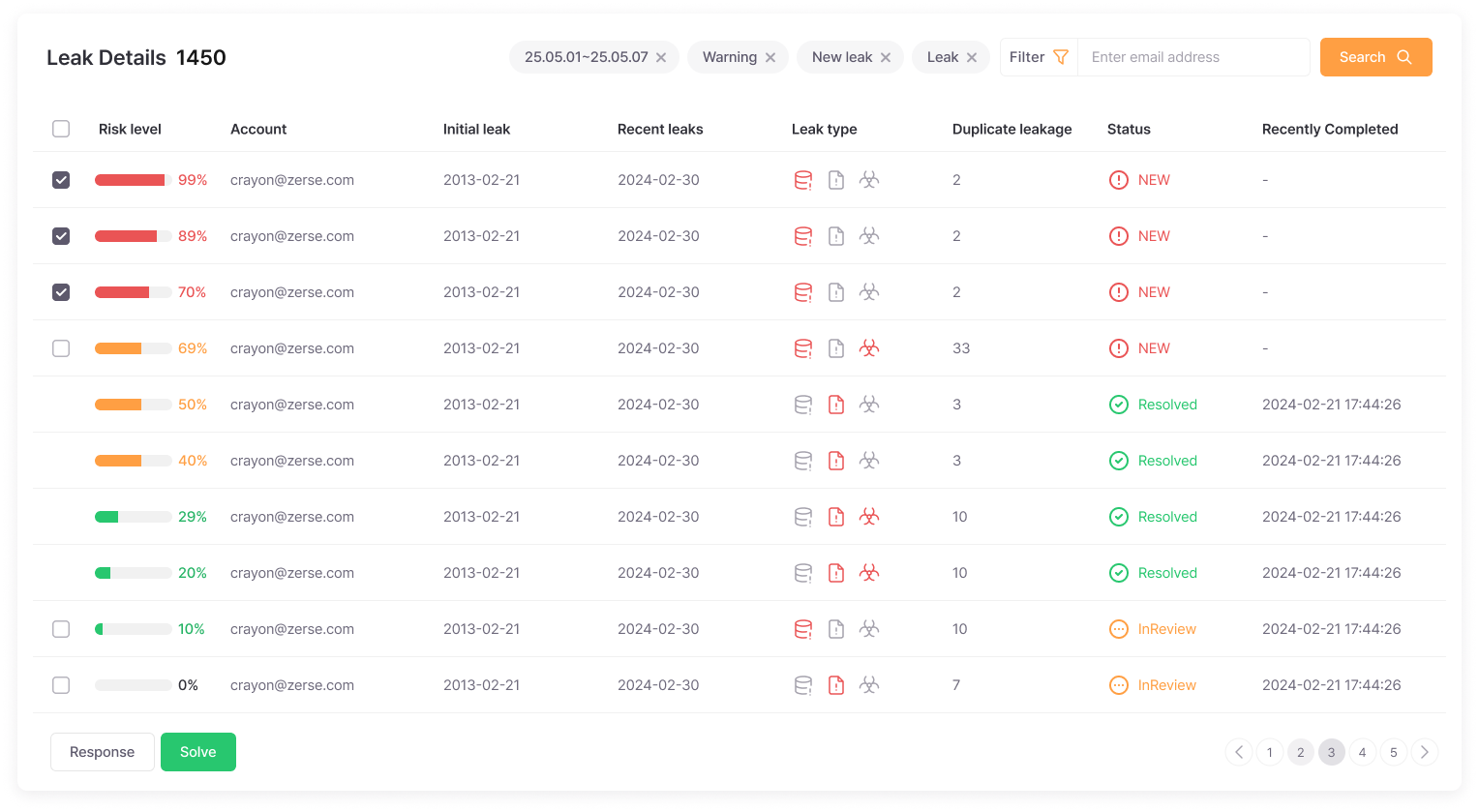
Leak Detail Information
Easily see at a glance which accounts were leaked when and how in Excel-like organized tables, making it easy to plan responses. Risk levels are color-coded, so you can prioritize red ones first, and clearly distinguish between unprocessed and already resolved items to easily track work progress.
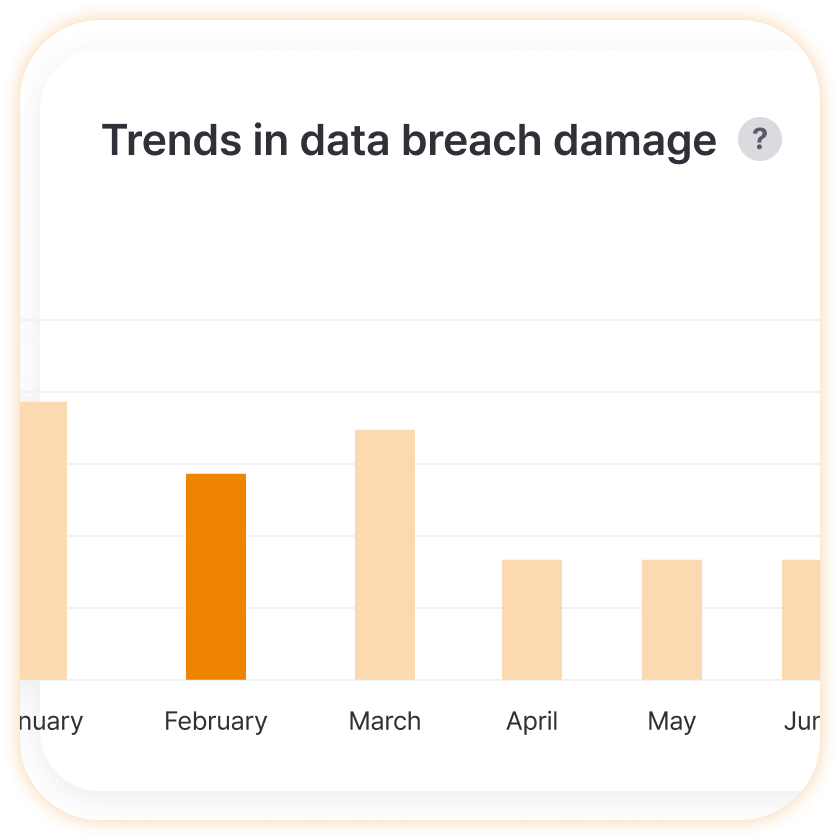
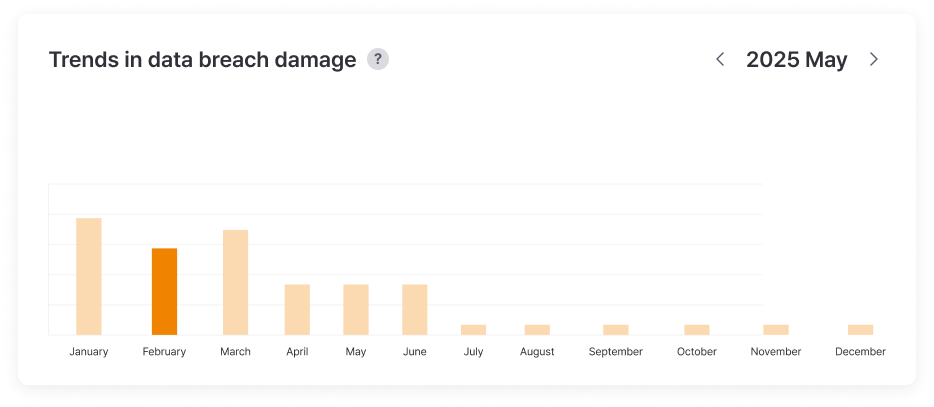
Leak Damage Trend
Easily identify whether this year’s situation is improving compared to last year and why leaks surged in specific months, helping establish long-term security strategies. Objectively compare effects before and after security system implementation, and accurately determine when to strengthen preventive measures by finding correlations with seasonal patterns or special events.
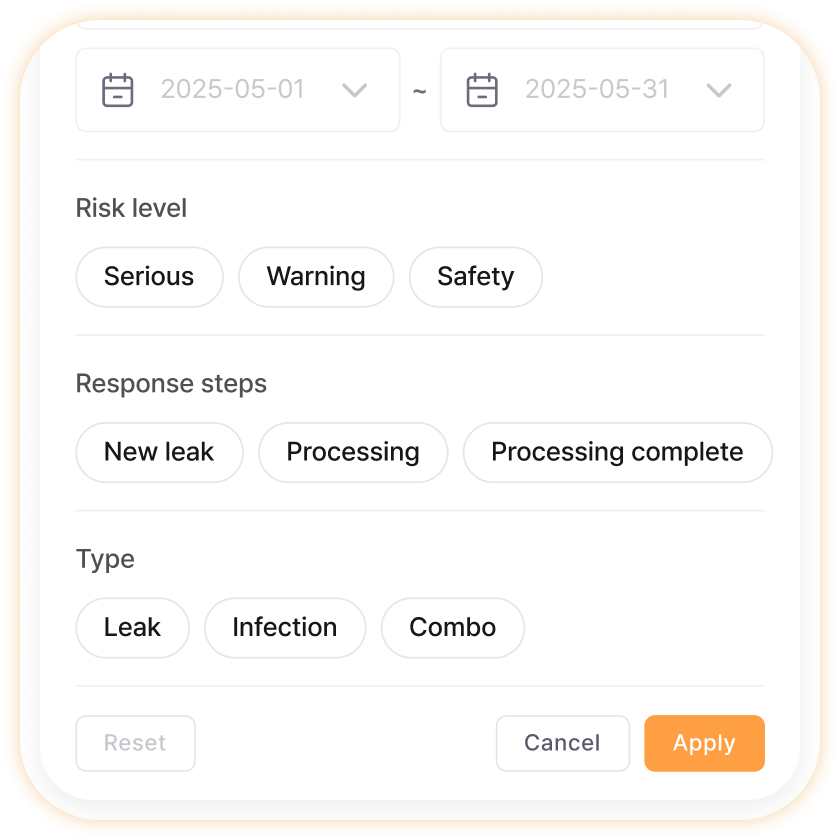
Leak Detail Information Filtering
Select and view only work you’re responsible for or information of interest, increasing work focus. For example, filtering only ‘this week’s critical-level unprocessed cases’ clearly shows only what needs to be done today, and filter status is displayed on screen so you don’t get confused about current viewing conditions, reducing mistakes.
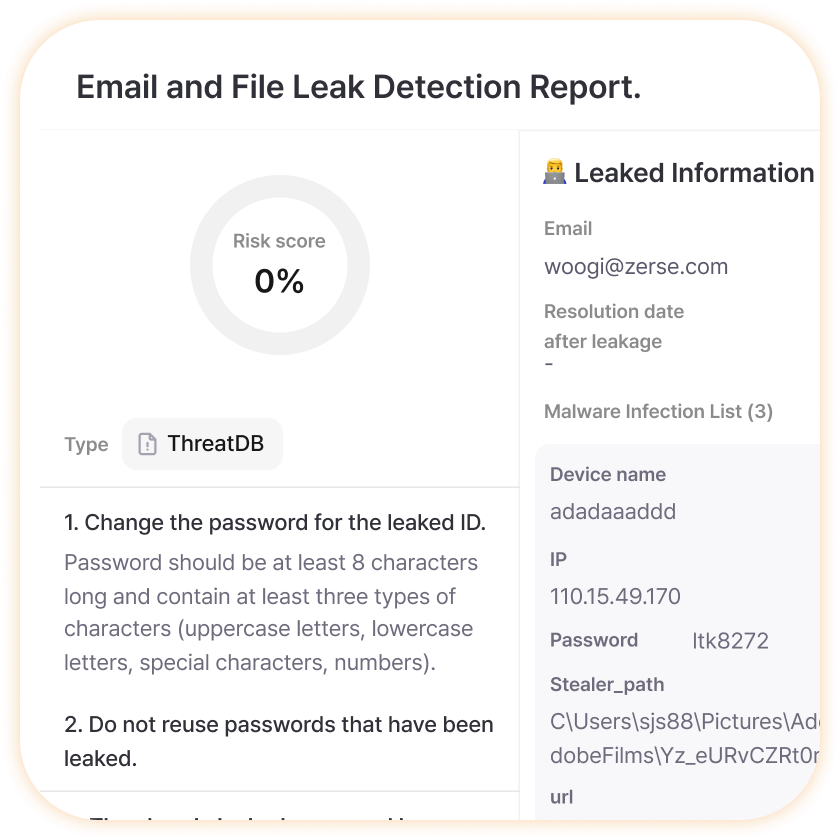
Email and File Leak Detection Report
Completely understand all information about a single leak incident on one page to systematically understand and respond to the entire incident. Track chronologically whether this account was leaked before, how many passwords were exposed, when it was resolved but leaked again, etc., to find and resolve fundamental security vulnerabilities.




