Summary Report
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

Key Features
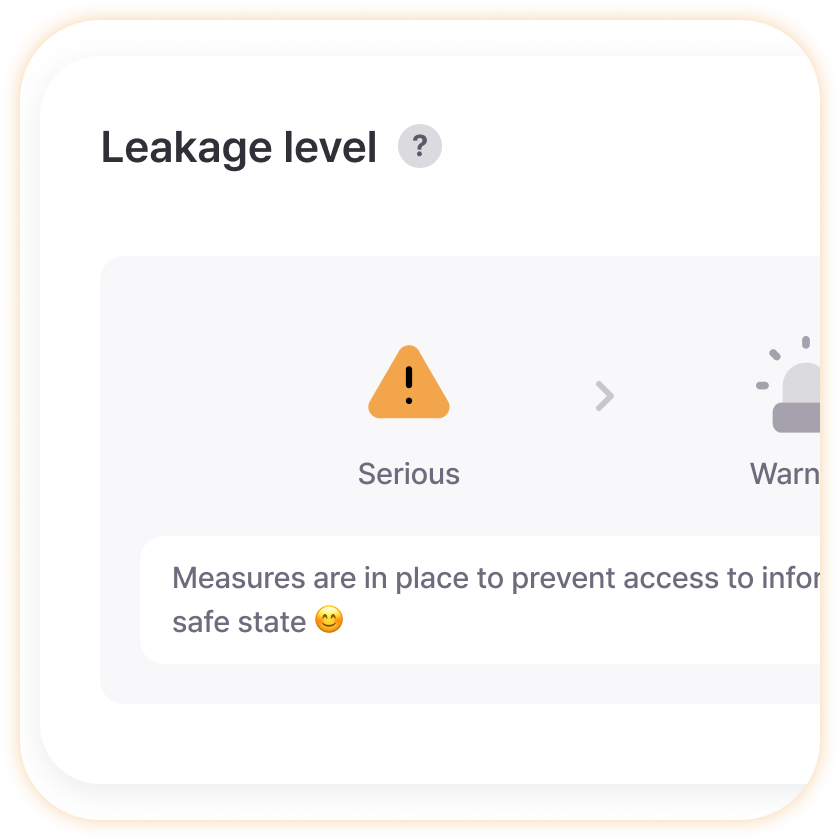
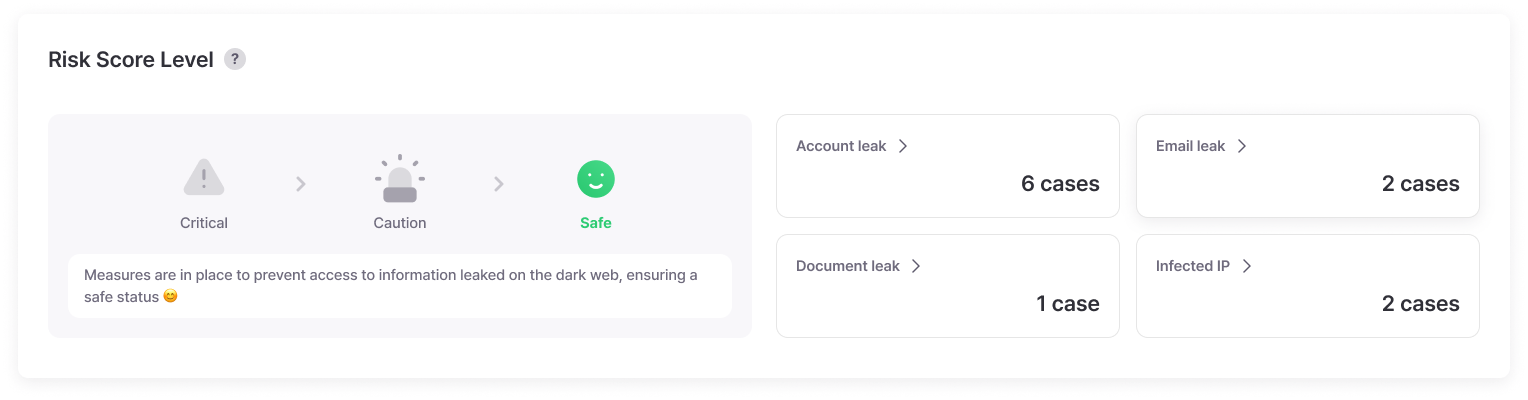
Dark Web Information Leak Level
Know how serious our company’s current situation is as simply as traffic lights without complex security terminology. Red light (critical) requires immediate emergency response activation, yellow light (warning) requires strengthened preventive measures, and green light (safe) means maintaining current security policies, allowing even non-experts to easily assess and respond to situations.

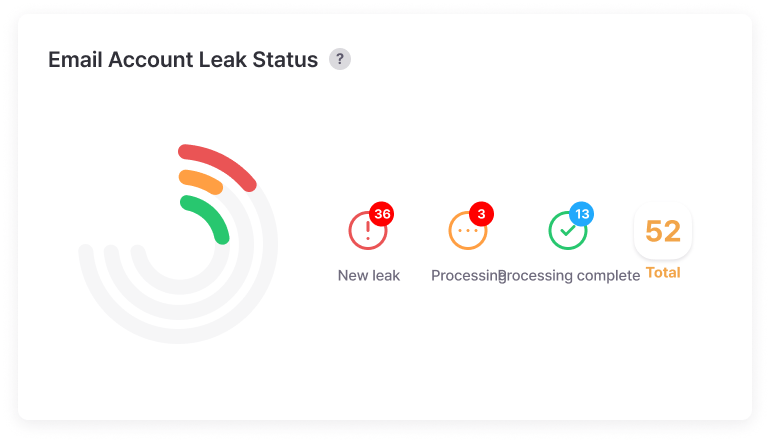
Email Account Leak Status
Easily see at a glance how many of the total leaks are still unprocessed and how many are currently being handled, making it easy to plan workload management and personnel deployment. Objectively measure team response performance through completion rates and use as indicators to prove security team work efficiency to management.
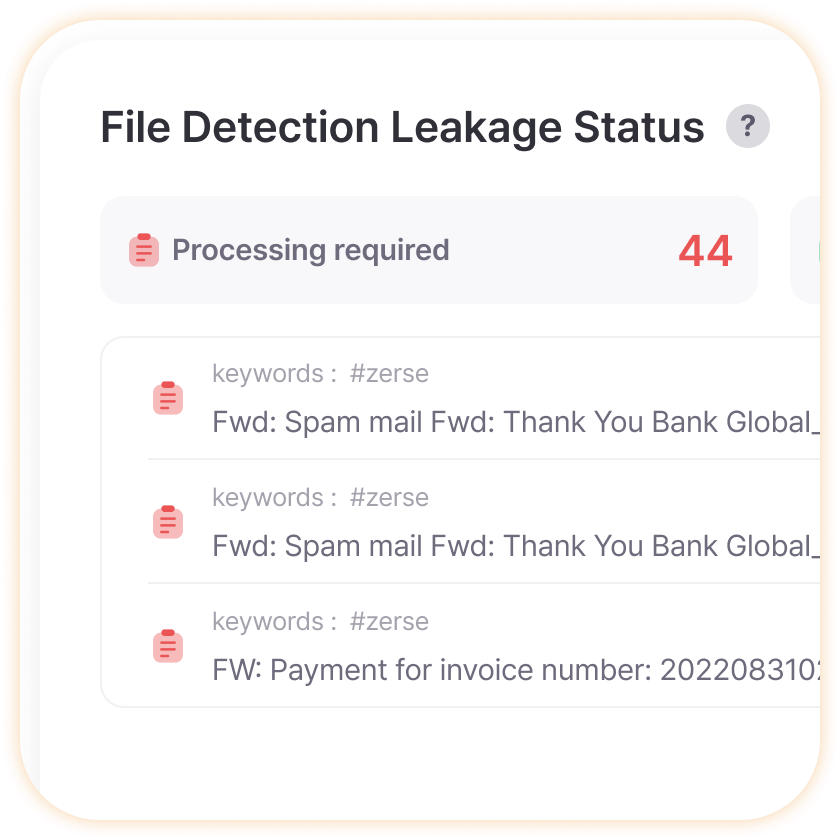
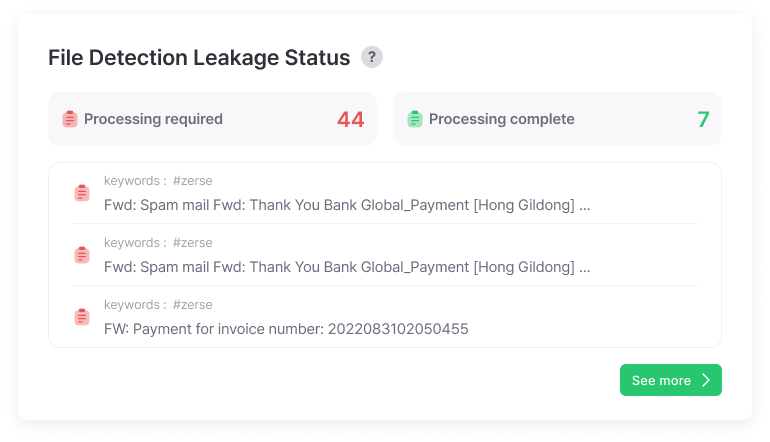
Email Attachment File Leak Detection Status
Preemptively identify whether important corporate confidential documents or files containing customer information have been leaked, enabling proactive response before major incidents occur. Automatically monitor leakage of files containing sensitive keywords like ‘contracts’, ‘blueprints’, ‘customer lists’, preventing losses from legal disputes or business secret leaks.
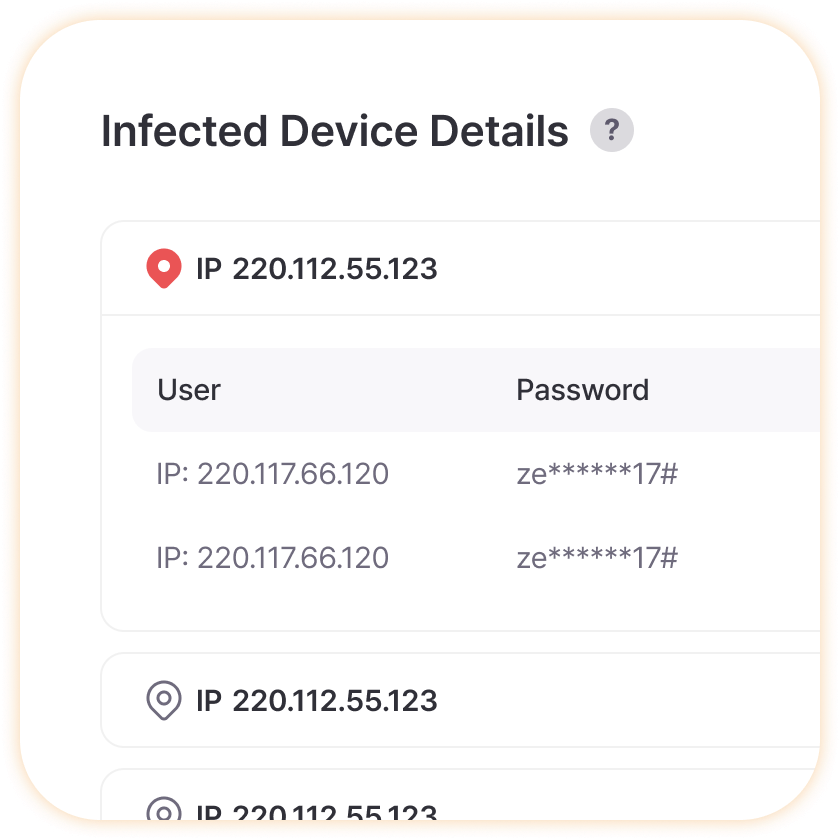
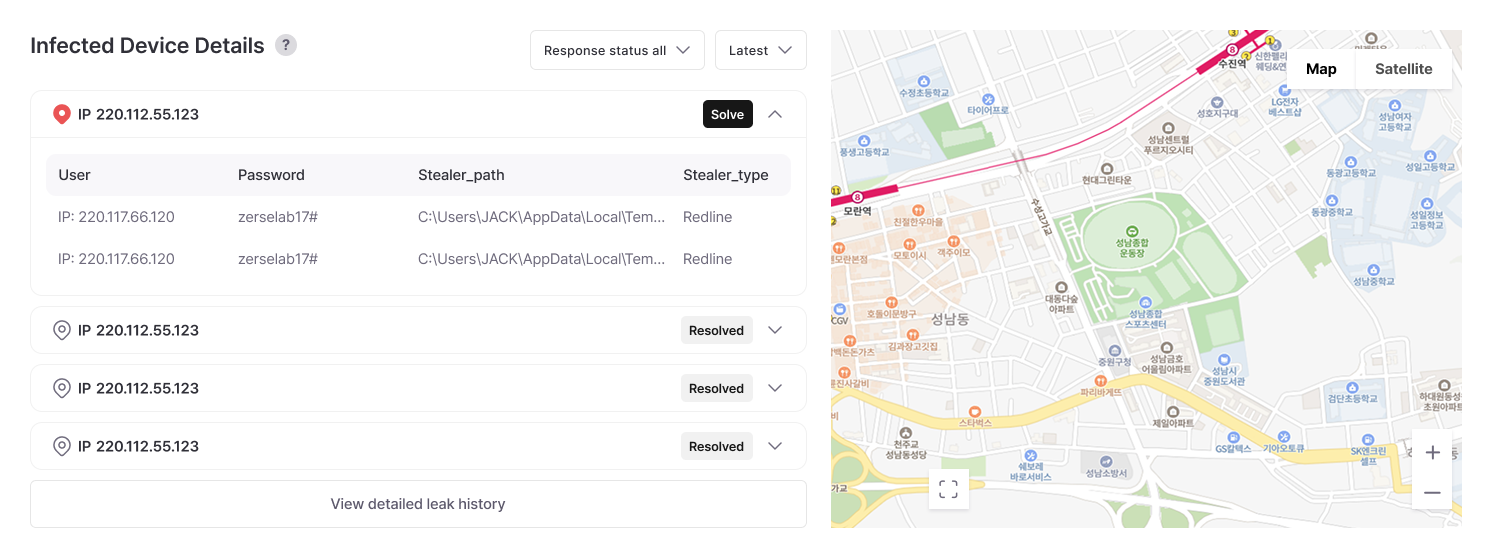
Detailed Report on Malware Infections
Visualize which regions have the most malware infections on maps to easily identify attack patterns. Specifically verify which account information was stolen from infected computers to immediately change passwords or block access for those accounts, and analyze infection paths to establish security measures preventing reinfection through the same methods.
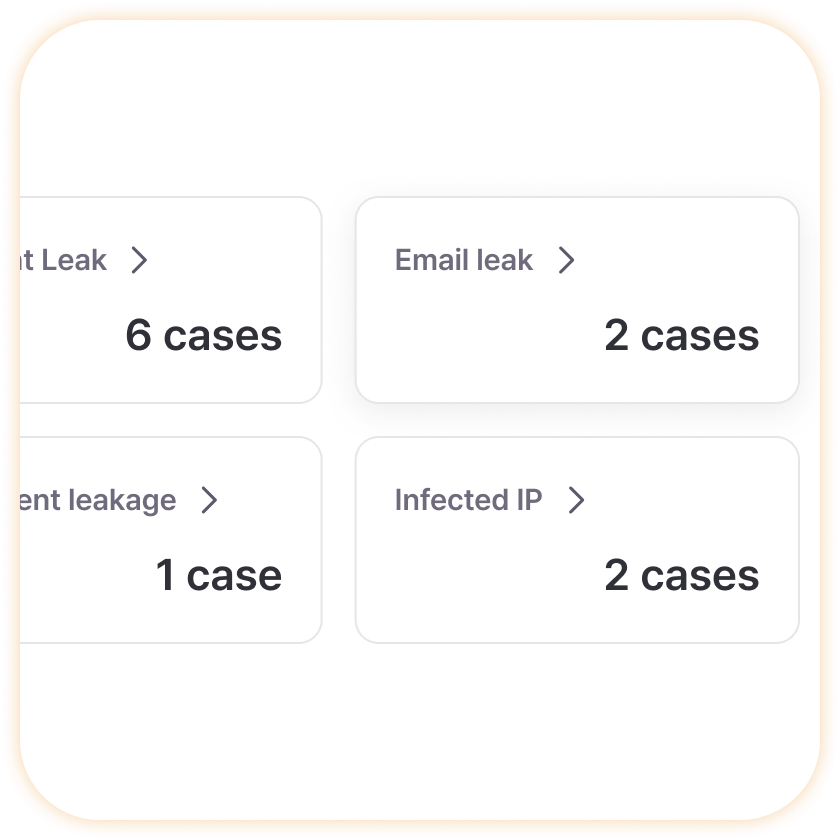
Leak Count
Access desired information directly with just a few clicks even during busy work, saving significant time. For example, clicking the ‘100 Document Leaks’ button filters and displays only document leak-related information, allowing immediate start of necessary work without searching through complex menus, greatly improving work efficiency.
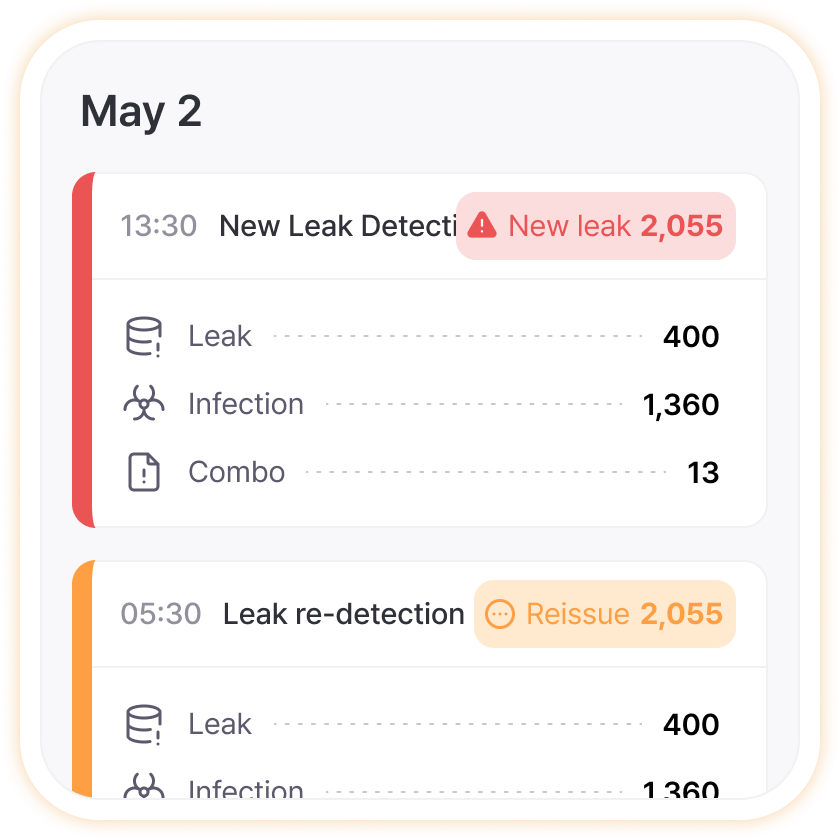
Leak Status - Timeline
Easily look back at what happened on specific dates, useful for incident cause analysis or response effectiveness verification. For example, if leaks suddenly increased last Tuesday, you can find correlations with system updates or external attacks that occurred that day, and apply successful response methods from certain days to other situations to improve response quality.
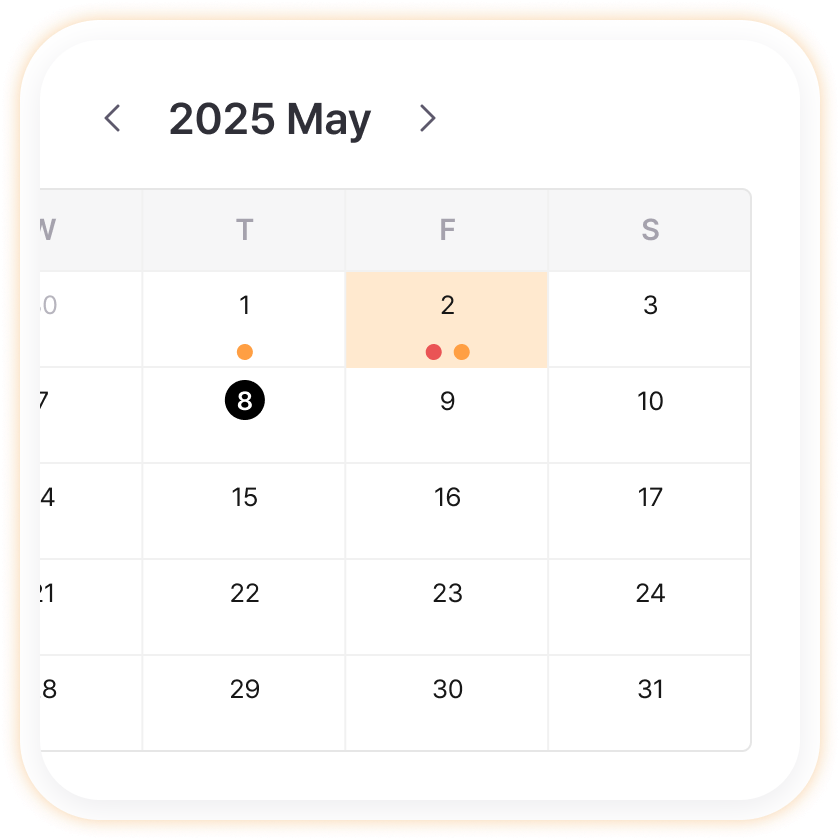
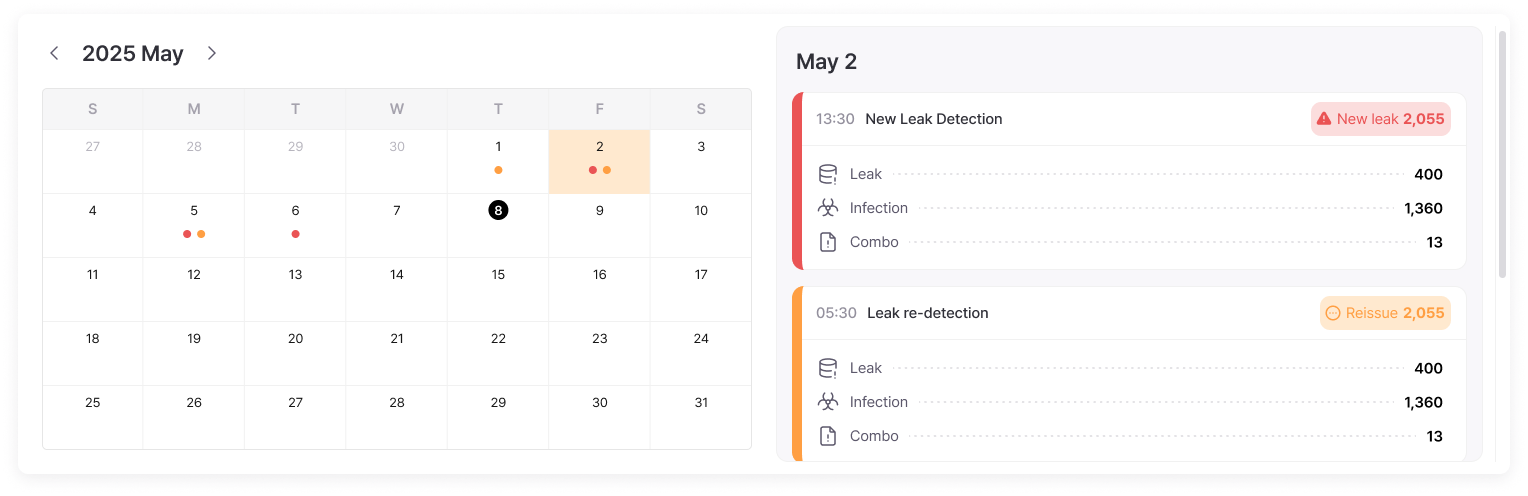
Leak Status - Calendar
View monthly security situations at a glance in calendar format to easily discover periodic patterns or specific weekday vulnerabilities. For example, if leaks increase every Friday, you can strengthen security checks before weekends, or if attacks occur intensively at month-end, you can strengthen monitoring during those periods to establish data-based prevention strategies.




