3.0
Respond swiftly to dark web information leaks with ZeroDarkWeb.
Accurately classify the level of information leaks on the dark web, and gain detailed insights from leaked email account status to malware infection states.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

Request a Demo for ZeroDarkWeb
"
"
"
"





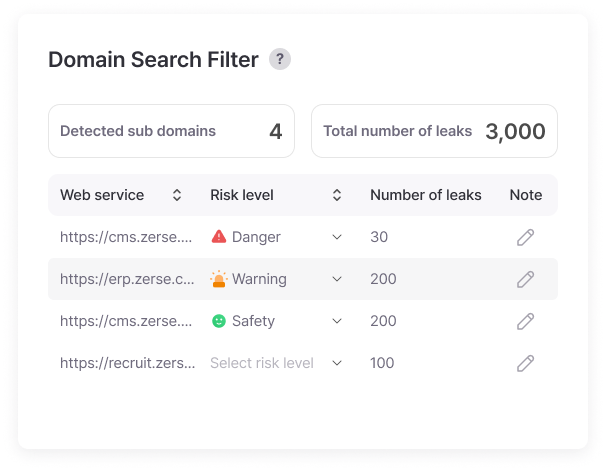
Web Domain (URL) Leak Detection
NEW
Integrated management of security status for all company-related websites and services on a single screen enables perfect security management.
Risk levels are color-coded for each service to instantly determine priorities, and step-by-step guides enable systematic security enhancement work even for non-security experts.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry




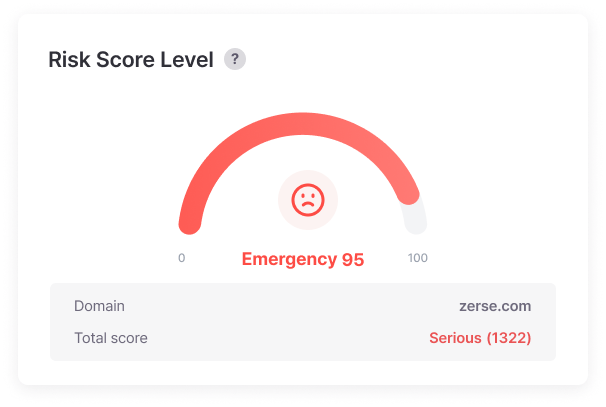
Summary Report
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

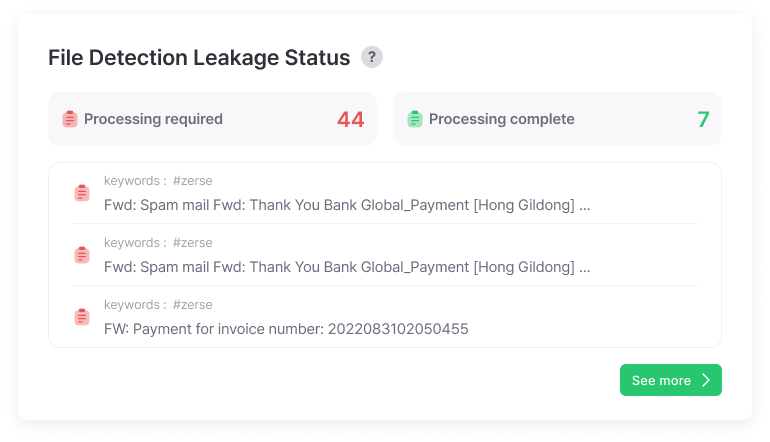
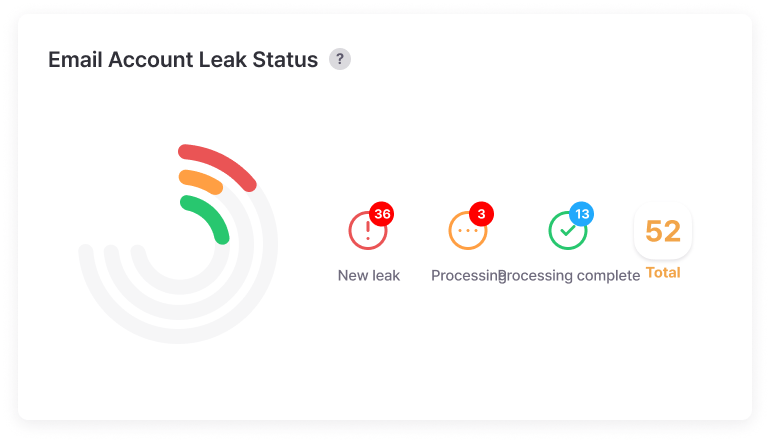
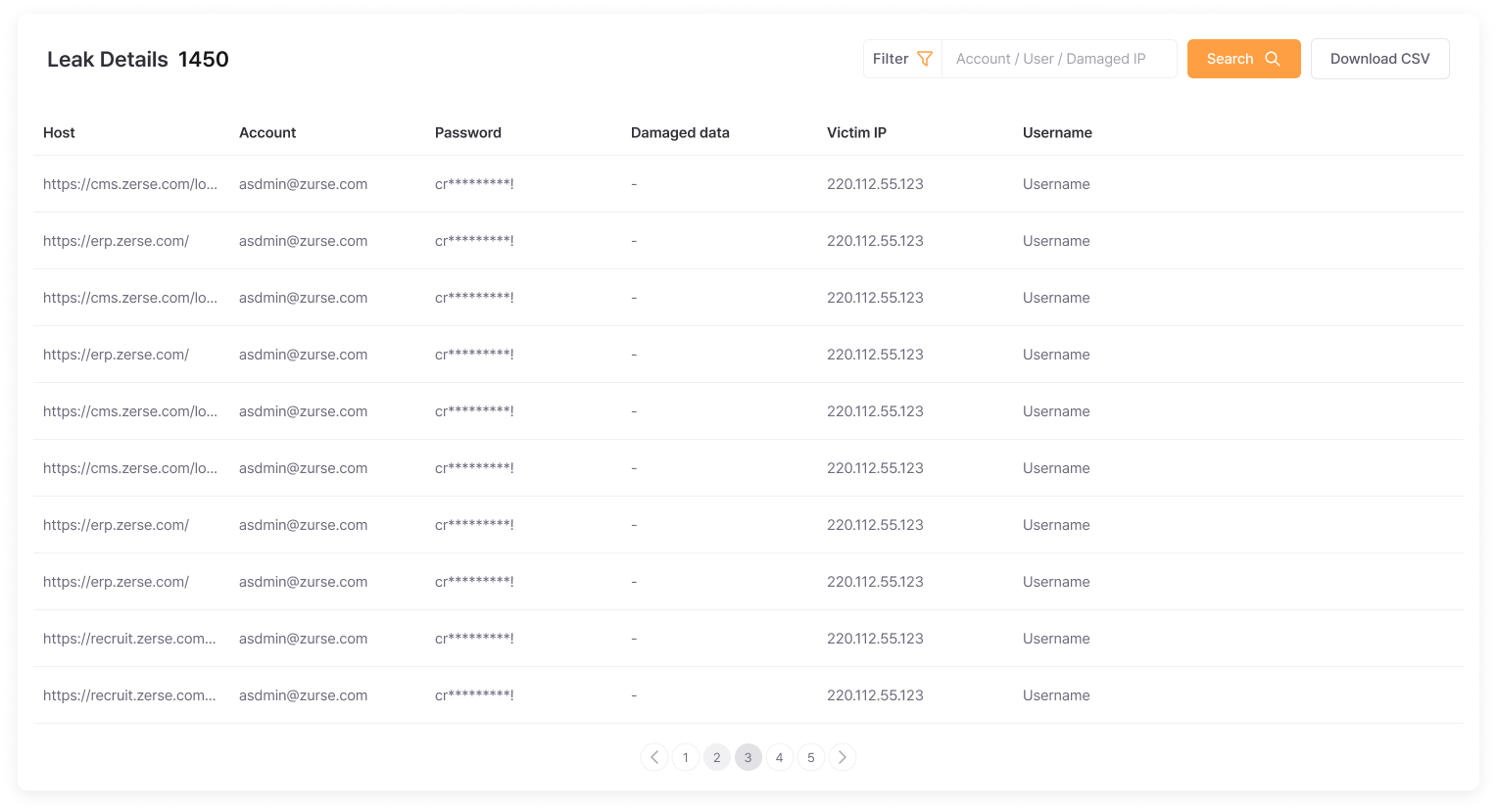
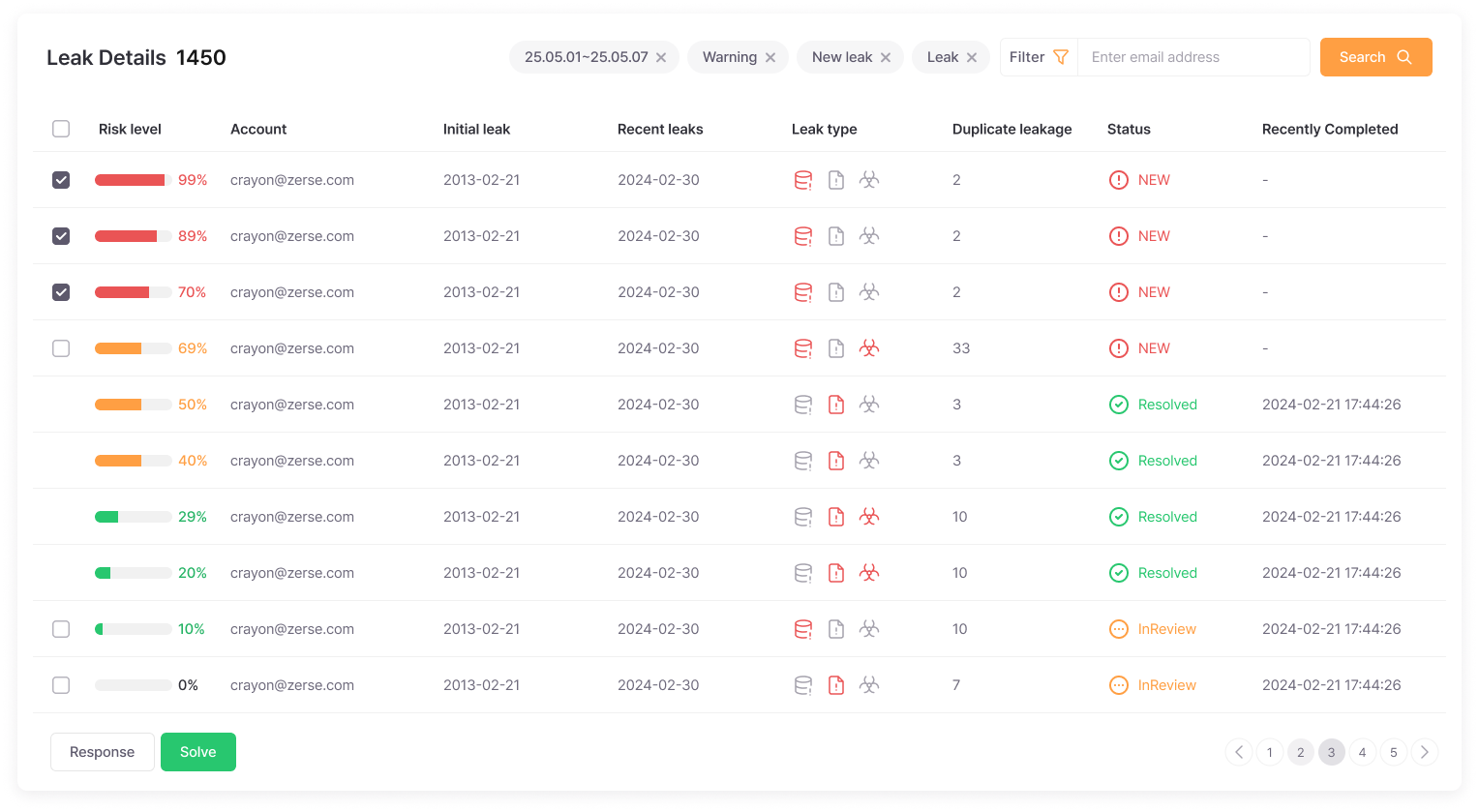
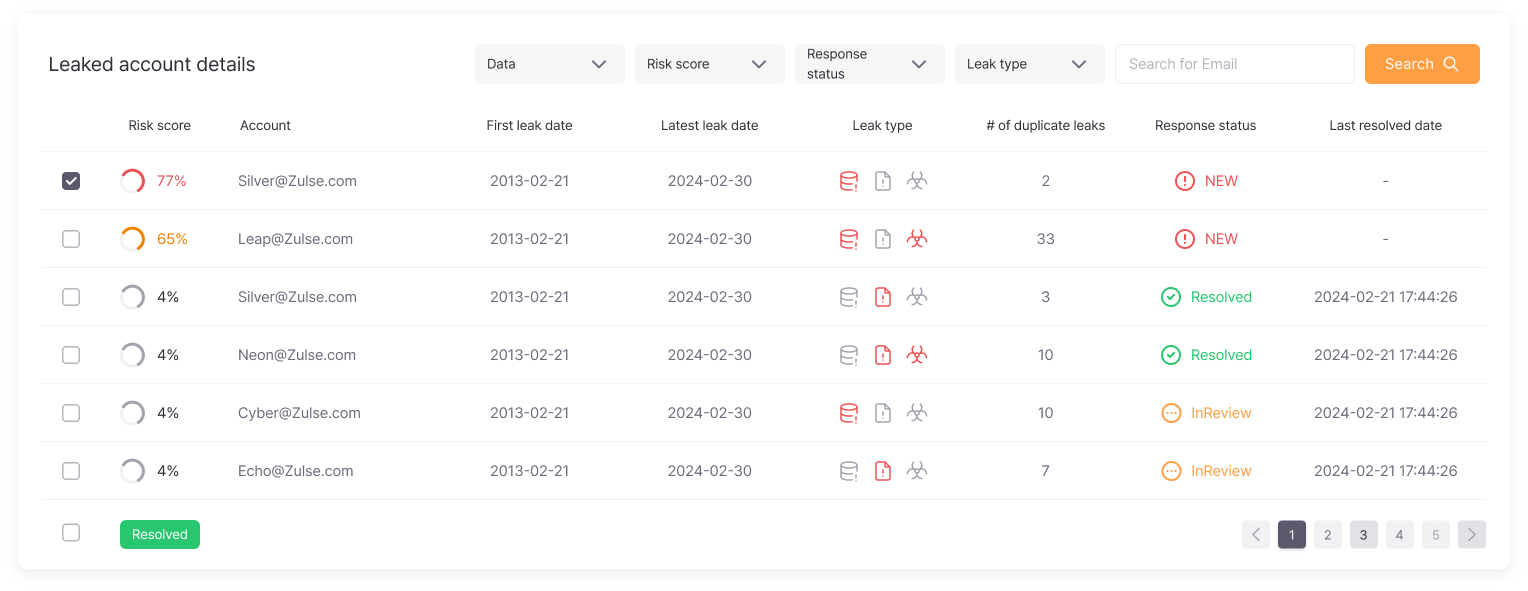
Leak Details
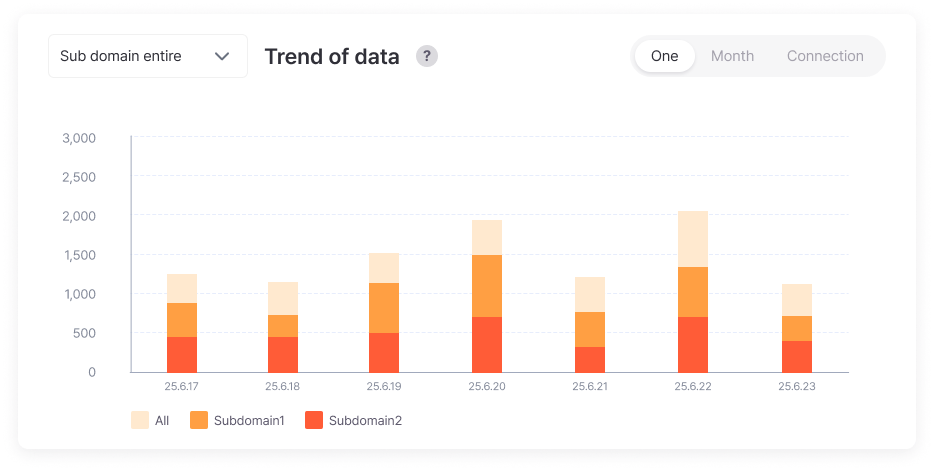
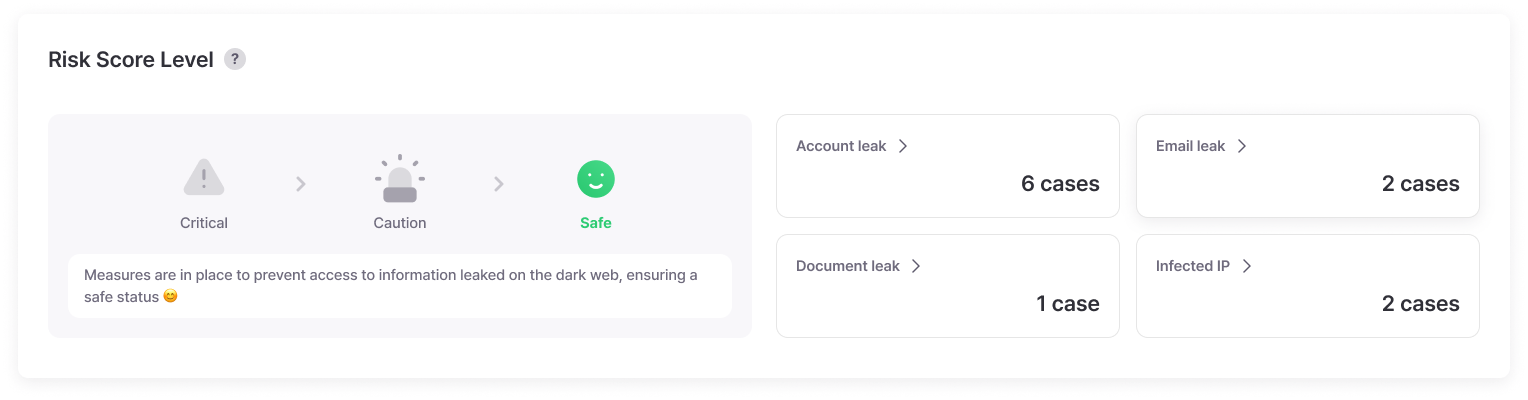
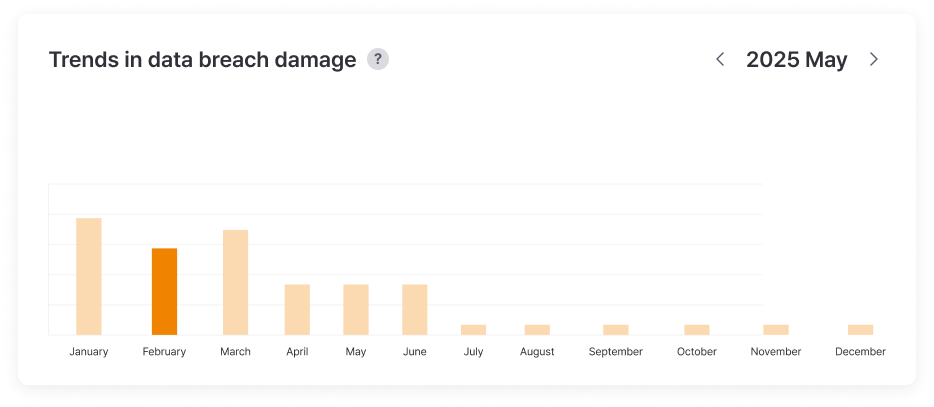
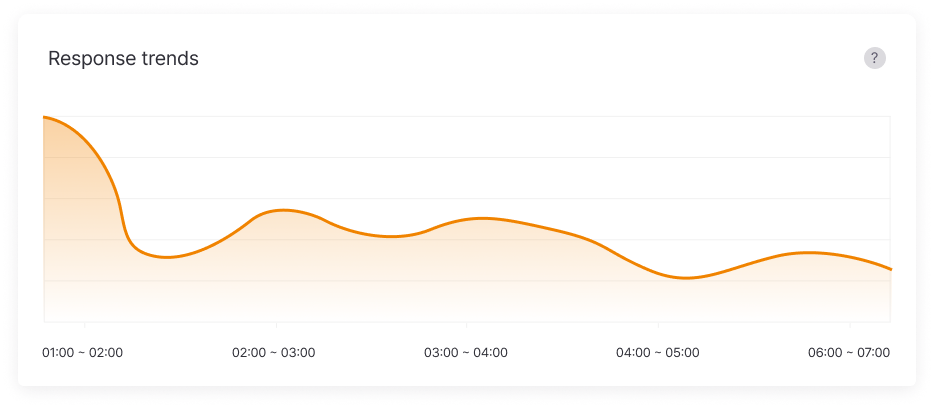
Provides severity levels and risk scores for leaked information, visualizing response trends and damage fluctuations.
Risk levels are scored to easily set priorities, and monthly/yearly leak trend analysis allows objective verification of security investment effectiveness.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

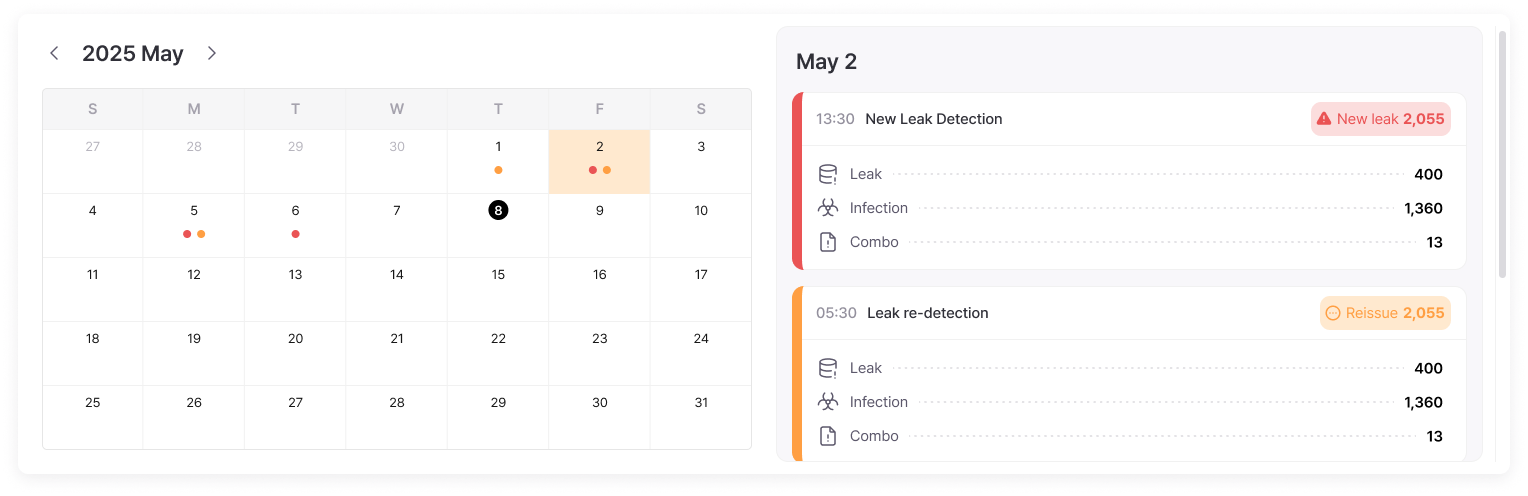
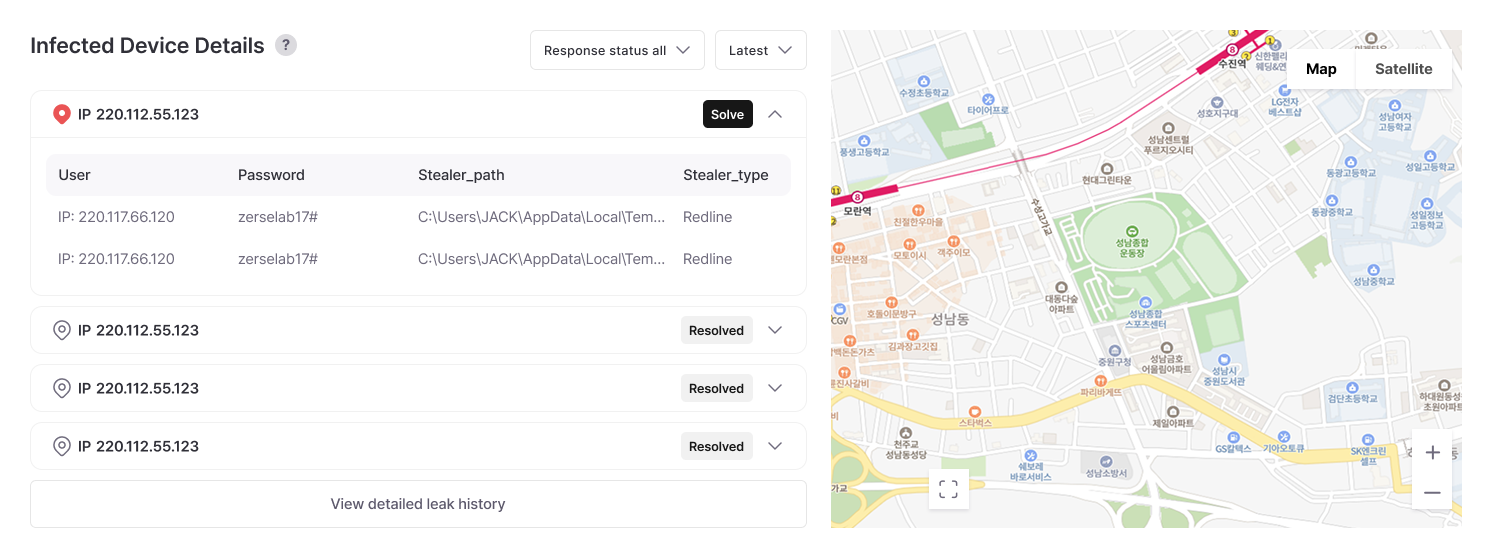
Response History
Accumulated past response cases enable immediate utilization of proven solutions when new problems arise, reducing response time and minimizing errors.
Learning from success and failure cases enables quick work adaptation for new employees, and discovering root causes of recurring problems allows development into a prevention-centered security system.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

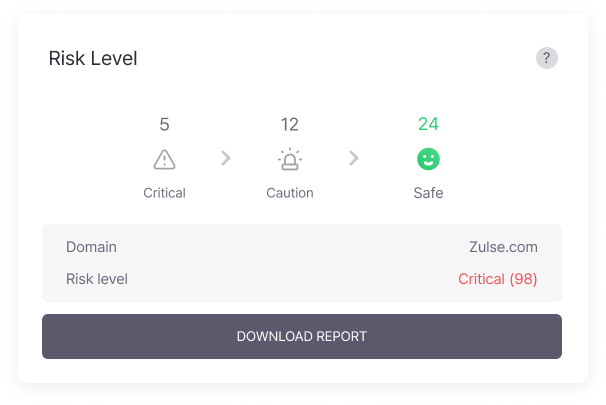
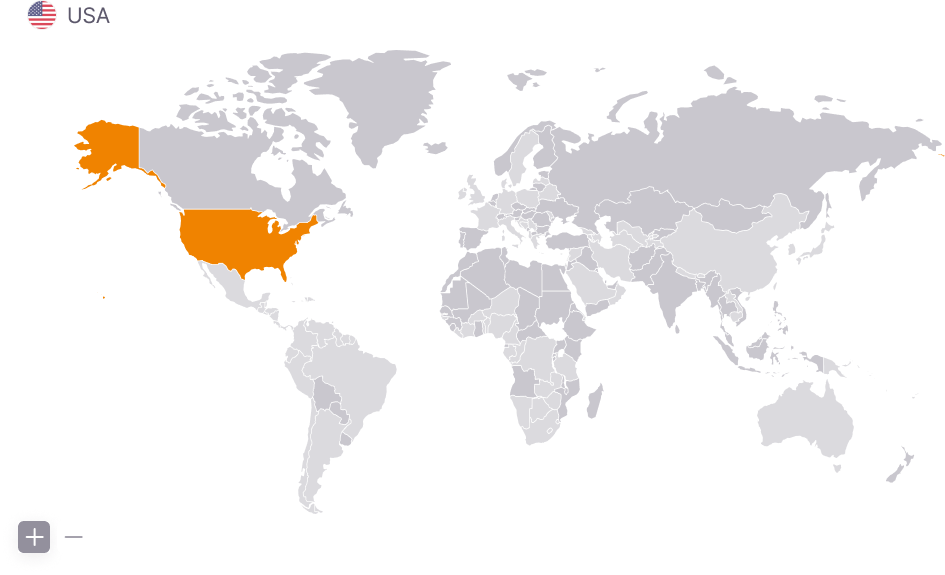
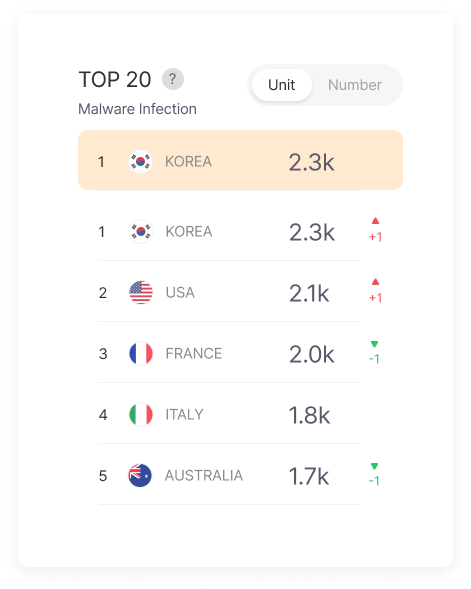
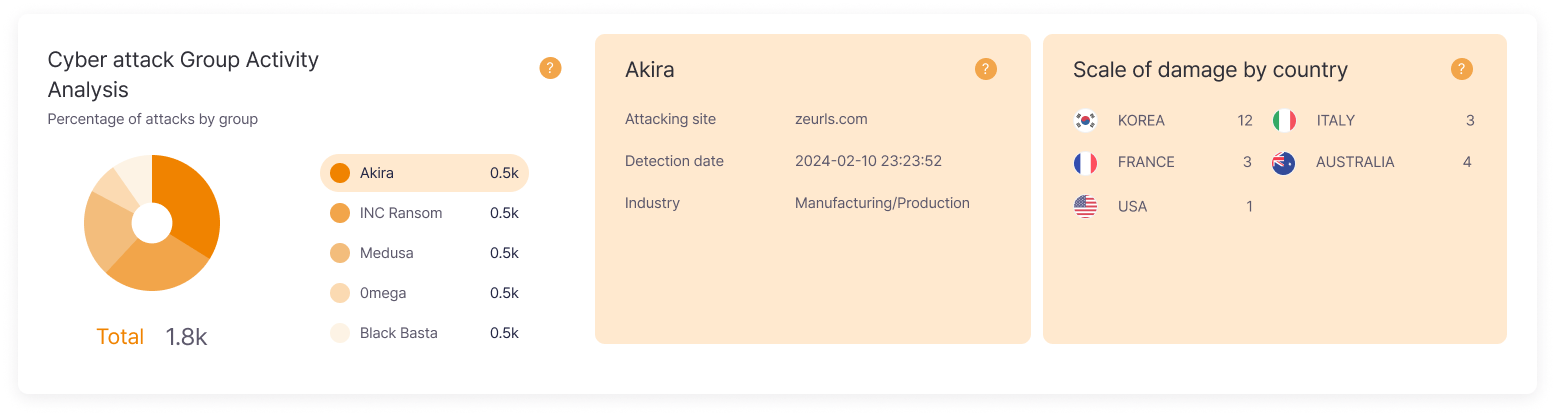
Global Cyber Attacks
By identifying global cyber attack trends in advance, you can prepare countermeasures before they reach our country, and establish customized defense strategies by pre-checking risk levels of overseas branches or partner companies.
For global business enterprises, you can pre-evaluate the cybersecurity environment of target countries and reflect security risks in business plans.
Global Cyber Attacks
Domain Leak Management
Summary Report
Leak Details
Response History
Subdomain Exploration
Docs / Email Leak Detection
Completed
Pending
Inquiry

ZeroDarkweb in numbers
Total Analyzed Data
322 B
Leaked Account Data
88 M
Leaks in the Sample Report
98.5 M
The Dark Web is the home ground of the ZeroDarkWeb.
You can address security issues with monitoring services without the need for a dark web specialist or advanced technical skills.

Web Domain (URL) Leak Detection
Automatically monitors all risks related to your company domain 24/7 and alerts you before they become major incidents.

Summary
Even busy executives can understand the severity of your company’s security situation in seconds and make immediate decisions.

Leak Details
Receive specific solutions for what and how to handle each leak incident, enabling immediate response without confusion.

Response History
Through past response cases, you can quickly apply proven solutions when new incidents occur, reducing processing time.

Global Cyber Attack Trends
Gain competitive advantage by identifying global cyber attack trends in advance and preparing countermeasures before they reach our country.